Audit events in your environment is crucial for the discovery and investigation of security incidents: it is also important to know the best practice for configuring the Windows Server 2016/2019 policy.
Here’s a list of my presonal tips which I normally implement in my organization.
DISCLAIMER: images are not from my lab (except for the log view), I took from internet
1. Basic audit events
First of all, open the GPO editor and go to this path
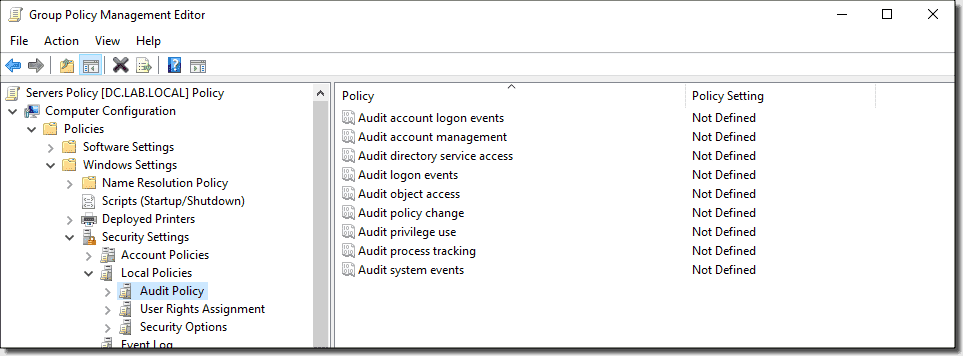
For each options, if enabled, you can choose what audit: success or failure events.
IMHO the minimum settings to enable and audit in both cases are:
- Audit account logon
- Audit account management
- Audit logon events
- Audit policies change
- Audit privileges use
- Audit system events
Please note: a properly configured audit policy generate a lot of events, especially on servers such as domain controllers or file servers that are frequently accessed. As you know, all these events are written to the Windows Security log and the default maximum log size, which is 128 MB, could only store a few hours.
Ideally, the best practice is to forward specific events to systems such as sysLog or other SIEM tools.
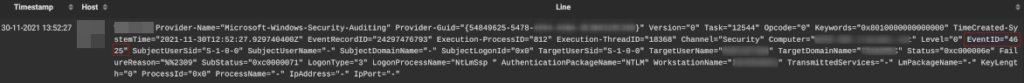
2. File server object access
IMHO it is important to audit all user actions concerning files and folders access.
In order to do that you’ve to enable – and set “success” and “failure” options – the “Audit Object Access” in the previous GPO path, then:
Go to “Security” tab, and click “Advanced”
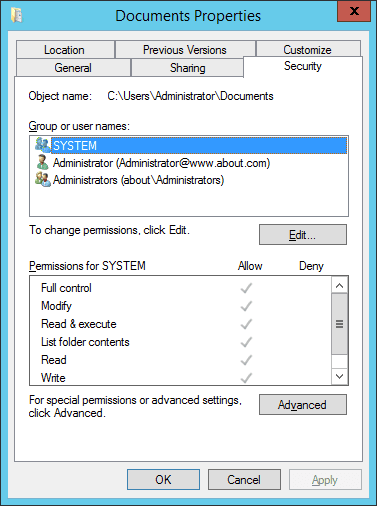
In “Advanced Security Settings” dialog box, select “Auditing” tab and click “add” on the bottom window
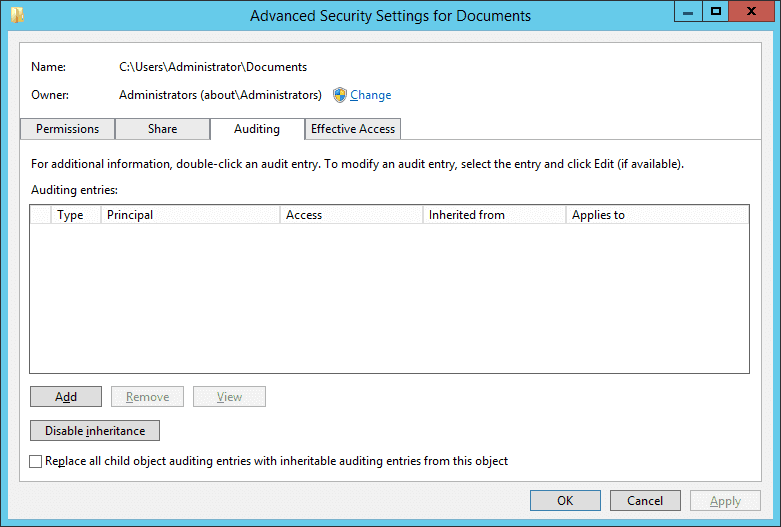
Click “Select a principal” link. It will shows “Select User” dialog box
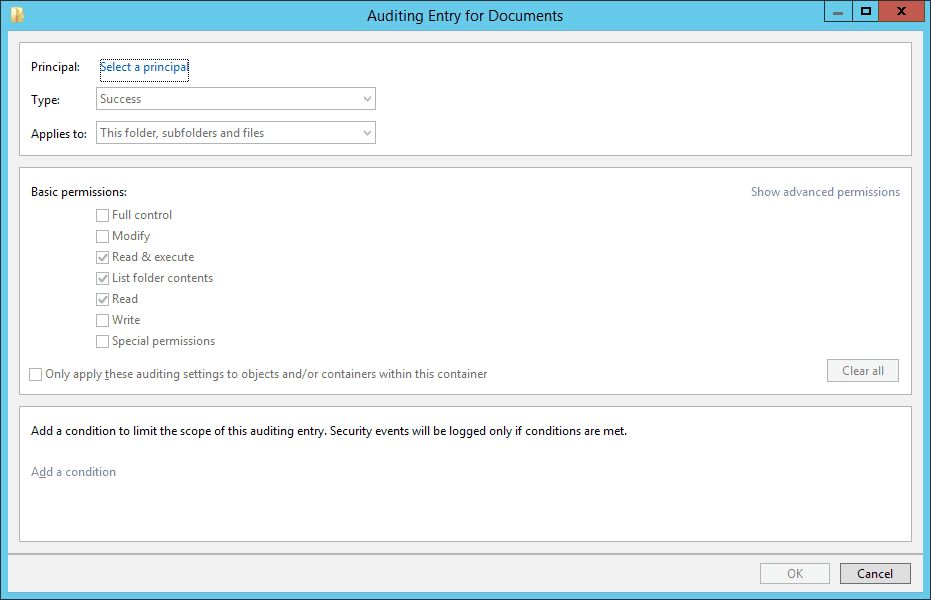
Type the name of the user/s which you want to monitor.
Alternatively, you can type “Everyone” to monitor every user accesses to this folder.
After that you’ll be back on the Audit window
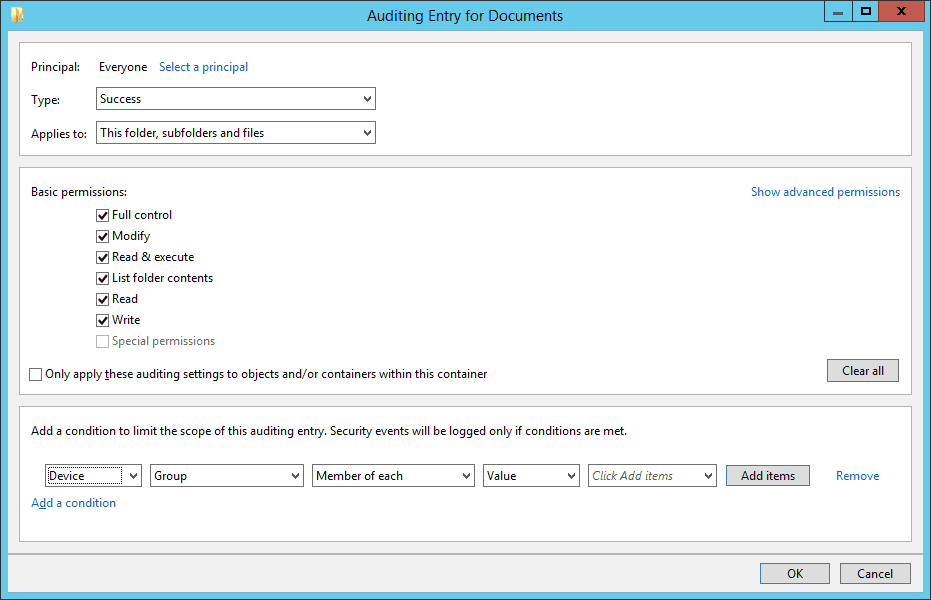
- Select “Both” in “Type” drop-down menu to monitor both “Success” and “Fail” accesses made to the folder.
- In “Applies to” drop-down menu, select “This folder, subfolders, and files”.
- Select “Full Control” or the appropriate permissions for auditing. It is advised to click “Show Advanced Permissions” and select all permissions.
- You can use “Add a condition” link at the bottom to limit the scope of this auditing entry. You can add multiple conditions, if required. This way the auditing will generate limited logs.
- Click “OK” to save the settings and close “Auditing Entry for ” window.
- Click “Apply” and “OK” to close “Advanced Security Settings for” window.
- Click “OK” to close the folder properties.
After auditing has been enabled, the logged events can be viewed in Event Viewer.
EOF